thick client application testing tools|thick client penetration testing methodology : exporting 1. Capturing the request via Echo Mirage. Echo Mirage enables intercepting non-HTTP traffic between the tested thick client and the local or remote server. Intercepting requests using this tool, give insight into what kind . Die Verfügbarkeit von Online Echtgeldspielen in Deutschland hat sich leider durch die Regulierung grundlegend geändert. Hier sind die wichtigsten Punkte, die ihr beachten . Ver mais
{plog:ftitle_list}
Resultado da Forgot your password? Log in. Don't have an account? Sign up
1. Capturing the request via Echo Mirage. Echo Mirage enables intercepting non-HTTP traffic between the tested thick client and the local or remote server. Intercepting requests using this tool, give insight into what kind . Understanding Thick Client Penetration Testing. Thick client applications, also known as desktop applications, are complete computing systems connected to a network. . and examining network communication to .
Applications such as Gtalk is a classic example of thick client applications. Traditionally, thick client applications are developed using some of the following technologies..NET; C /C++; Microsoft Silverlight; Java applets etc. Common thick client application designs. We usually see two types of thick client application designs as discussed in .
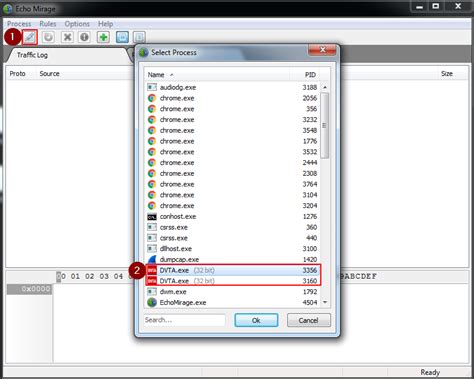
We use them daily in the form of web browsers, games, desktop music players, messenger programs, video conferencing tools like Zoom, etc. In simple terms, Thick Client Applications are Desktop applications based on . The client sends the password “p@ssw0rd” in the following line. Using Tool Echo Mirage. Echo Mirage is a local proxy tool used to intercept and modify TCP payloads for local Windows applications. Learn about Echo Mirage, a freeware tool that hooks into an application’s process to monitor network interactions.
OWASP ZAP, on the other hand, focuses on web application security and provides a comprehensive set of tools for testing thick client applications. Its automated scanning capabilities help identify common vulnerabilities, such as cross-site scripting (XSS) and SQL injection, in both the client-side and server-side components of the application.Tools For performing Thick client Pen-testing: - Dynamic Testing / Functional Level Testing. Proxy Interception: Proxy-Aware Thick Client: If Thick Client application has a built-in feature to set up a proxy server, then it is known as a proxy-aware Thick Client.
thick client testing tool
Tools Used. UISpy; Winspy++; Window Detective; Snoop WPF; FILE TESTING. Test For Files Permission. Check permission for each and every file and folder; Test For File Continuity. Check strong naming; Authenticate code signing; Test For File Content Debugging. Look for sensitive information on the file system (symbols, sensitive data, passwords .
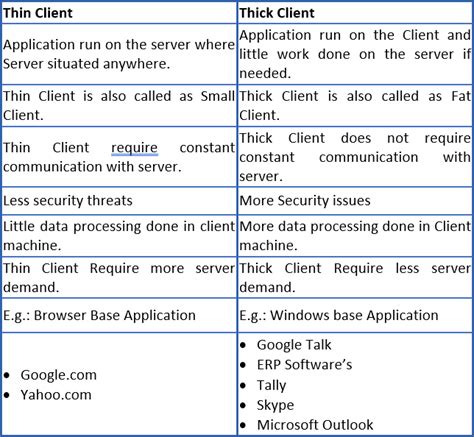
Referenced under multiple names, such as: Fat client/Heavy client/Rich client/Thick client, such applications follow a client–server architecture. For an easy to understand approach, thick clients are applications which are deployed locally on our systems. Such as skype/ outlook. Thick clients can be developed using multiple languages such as . Latest Rankings: Detailed review and comparison of the top Performance and Load Testing Tools in 2024. Given below is a comprehensive list of the most widely used Performance Testing tools for measuring web application performance and load stress capacity. These load testing tools will ensure your application’s performance in peak traffic .
Tools Used in Thick Client Penetration Testing. . Burp Suite can be adapted for testing thick client applications, especially those with communication to backend servers.
Tools Used to Test Thick Client Applications: There are a lot fewer tools available for evaluating thick clients than there are for testing web-based programs. Many tools are no longer actively developed, while others have been migrated to online/mobile contexts. These are the tools used for testing thick client applications: 1.
thick client pentest checklist
This is an entry level to intermediate level course and we encourage you to take this course if you are interested to learn Thick Client Application Security. This course uses a modified version of vulnerable Thick Client Application called DVTA to demonstrate how thick client application vulnerabilities can be identified and exploited.
Testing thick client applications, for example, requires patience and a systematic approach, and simple automated assessment scanning does not suffice. A custom set-up is often necessary, as well as specialized tools. The architecture of thick clients Two-Tier architecture.It represents the most common security risks identified in thick client applications. . guidance in early stages of Software Development Lifecycle (SDLC) to avoid common vulnerabilities in thick client applications. . Security Testing Approch. Example. Put whatever you like here: news, screenshots, features, supporters, or remove this file .
With thick client applications increasingly relying on APIs for communication, there’s a growing focus on API security testing tools. These tools assess the security of the APIs integrated into thick client architectures, . Thick clients are also referred to as heavy or fat clients. Thick clients are not dependent on the server’s applications. They have their own operating system and software applications. They have high flexibility and .
Securityium's thorough Thick Client Penetration Testing identifies and mitigates vulnerabilities effectively for robust application security. . Tools Used : In our Thick Client Penetration Testing process, we use a diverse set of tools to ensure a thorough and effective assessment. Tools such as Insomnia, Dirb, BurpSuite, Wireshark, Echo . The Thick Client is also known as the “Fat Client”, “Rich Client” or “Heavy Client” Application. Few examples of thick client applications are Spotify, outlook, ERP Software, skype .
I have a thick client application to be tested. We need to downlod the jnlp file and then launch it, supply required credentials and click submit. It then launches the application. I'm newbie to performance testing and want to performance test this application. Which open source tool will be useful, which is the best tool for testing thick clients?Companies should adopt this document and start the process of ensuring that their desktop applications / thick-clients minimize these risks. Using the OWASP Top 10 is perhaps the most effective first step towards changing the software development culture within your organization into one that produces more secure code. What is Thick Client Penetration Testing? Thick client penetration testing (TCPT) is a type of security assessment that focuses on identifying and exploiting vulnerabilities in thick client applications. Thick clients are software applications that are installed on a user’s computer and run locally.Thick Client penetration testing is an ethical hacking security assessment carried out to uncover vulnerabilities in the thick client software application, network traffic, and backend interface and prioritize remediation efforts to mitigate cyber risks.
thick client penetration testing tools
The security analysis on the thick client application is always exciting because of its complexity, varying kind of architecture and protocols used to communicate with the external systems. This playlist has a list of free videos from our flagship course "Mastering Thick Client Application Penetration Testing".If you are interested in viewing th.

Welcome to the part 7 of Practical Thick Client Application Penetration Testing using Damn Vulnerable Thick Client App (DVTA). In the previous article, we have discussed how to perform .NET application patching using ildasm and ilasm utilities to modify the functionality of a .NET assembly. In this article, we will discuss DLL Hijacking in . 5. Vulnerable Labs of thick client application. What is a Thick Client? A thick client, also known as a fat client or rich client, is a software application that performs most of its operations . Examples of the thick clients are video editing software, video conference software, MS Office, MS Outlook, etc. In this article, we will see the procedure to be followed, vulnerabilities, and tools used for accessing the security of thick client applications.
red sea salinity refractometer
refractometer 0 10
Test your knowledge of the game, and learn some interestin.
thick client application testing tools|thick client penetration testing methodology